Introduction
Amazon EC2 (Elastic Compute Cloud) is a core service in AWS that provides scalable computing capacity in the cloud. To ensure security and controlled access, AWS uses Security Groups, which act as virtual firewalls to regulate inbound and outbound traffic for EC2 instances. In this blog, we’ll explore how to launch an EC2 instance and configure Security Groups step by step.
What is an EC2 Instance?
EC2 instances are virtual machines that run in the AWS cloud, allowing users to host applications, deploy services, and manage infrastructure easily.
What are Security Groups?
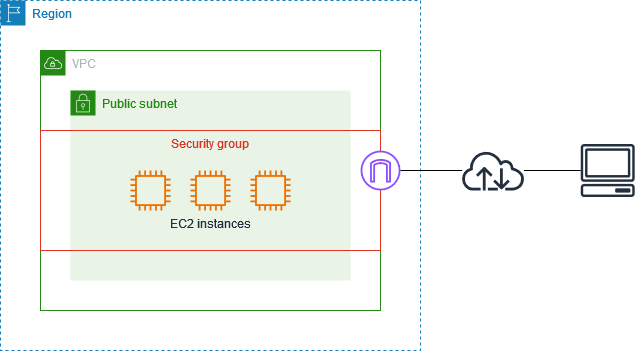
Security Groups define rules for network traffic to and from your EC2 instances. They help control:
Inbound traffic: Defines what connections are allowed to reach the instance.
Outbound traffic: Defines what connections the instance can initiate.
Think of Security Groups as firewalls that protect your EC2 instances from unauthorized access while allowing necessary traffic.
Step-by-Step Guide to Launch an EC2 Instance and Configure Security Groups
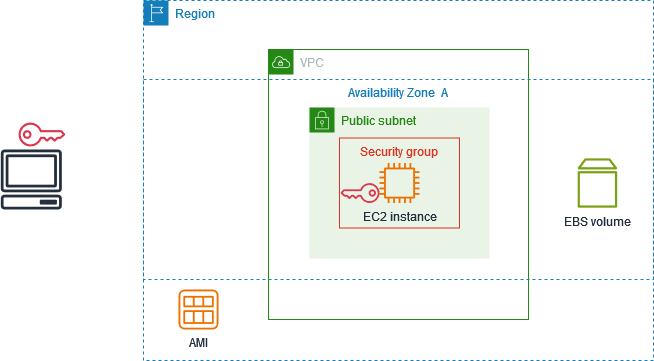
1️⃣ Sign in to AWS Console
Go to the AWS Management Console.
Navigate to the EC2 Dashboard.
2️⃣ Launch a New EC2 Instance
Click Launch Instance.
Choose an Amazon Machine Image (AMI) like Amazon Linux 2 or Ubuntu.
Select an Instance Type (For free tier:
t2.micro).Configure instance settings as required.
3️⃣ Configure Security Groups 🔐
Security Groups help define which ports and protocols are accessible to and from your EC2 instance.
Create a new Security Group or use an existing one.
Set inbound rules:
SSH (Port 22): Allow only your IP for secure remote access.
HTTP (Port 80): Allow access if running a web server.
HTTPS (Port 443): Allow secure web traffic.
Set outbound rules: By default, allow all traffic.
4️⃣ Launch and Connect to the Instance
Click Launch and select/create a key pair (
.pemfile) for SSH access.Use SSH to connect:
ssh -i your-key.pem ec2-user@your-instance-ipVerify security settings:
netstat -tulnp
5️⃣ Modify Security Groups as Needed
Navigate to EC2 Dashboard → Security Groups.
Edit inbound/outbound rules based on application requirements.
Best Practices for Security Groups
✅ Limit SSH access to your IP instead of allowing global access (0.0.0.0/0).
✅ Use IAM roles for access control instead of opening unnecessary ports.
✅ Enable AWS CloudWatch logs to monitor and analyze traffic patterns.
✅ Regularly review security rules to minimize vulnerabilities.
References & Video Tutorials 🎥
📌 AWS Documentation: EC2 User Guide
📌 Video Tutorial: How to Launch an EC2 Instance - in Hindi
📌 Video Tutorial: How to Launch an EC2 Instance - in English
📌 AWS Security Best Practices: AWS Security Whitepaper
Conclusion
By following these steps, you can securely launch and manage AWS EC2 instances with properly configured Security Groups. Mastering these concepts is essential for cloud security and DevOps best practices.
🚀 Let’s Discuss! What best practices do you follow for securing AWS EC2 instances? Drop your thoughts below! 👇
